Documentation and Knowledgebase
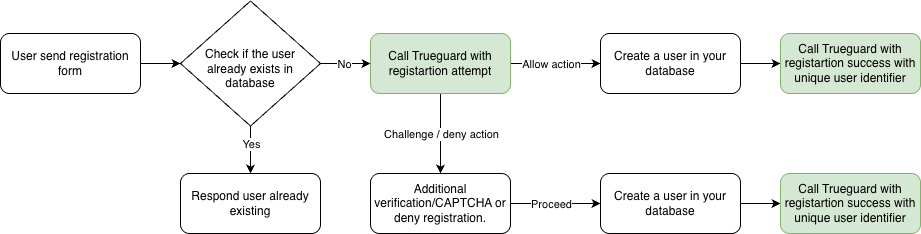
Reccomended flow with Trueguard
How we recommend you use Trueguard to protect your business against fraudlent users from registering.
- The user send the filled out the registration form with details like name,email, and password.
- Your system checks whether the email (or another identifier) is already linked to an existing account.
- If no match is found, send a registration attempt event to Trueguard to receive a risk evaluation.
- Based on Trueguard's response, decide the next step:
- Allow: Create the user account in your database, then notify Trueguard with a registration success event that includes the user's unique identifier.
- Challenge / Deny: Handle the case according to your flow - for example, ask for extra verification, or block the attempt.
Trueguard signals
Trueguard detects a variety of signals during an event. Each signal highlights a potentially risky property or behavior that can be used to block, challenge, or further review suspicious activity.
Email Intelligence
- disposable_email - The email address comes from a temporary or disposable provider, often used to bypass verification or create multiple accounts.
- multiple_aliases - Variations of the same email are being used (e.g.
test@gmail.comandtest+2@gmail.com), often to create duplicate accounts or abuse promotions. - invalid_email - The email domain does not have valid DNS records, meaning it cannot receive legitimate messages and is likely fake.
IP & Network Intelligence
- vpn_ip - The request originates from a VPN, masking the user's true location or identity.
- proxy_ip - The IP address is routed through a proxy service, commonly used to anonymize traffic.
- high_risk_ip - The IP address is linked to malicious activity, spam, or fraud attempts, or originates from data centers where legitimate users rarely connect.
Device & Browser Intelligence
- multiple_accounts_per_device - A single device is tied to multiple user accounts, often an indicator of fraudulent activity.
- bot_signals - Automation patterns (non-human interactions) are detected, suggesting bot-driven behavior.
- incognito_browser - The user is browsing in private/incognito mode, commonly used to avoid tracking or fingerprinting.
- high_risk_browser - The browser environment shows signs of manipulation or spoofing, such as automation tools, injected scripts, or fingerprinting evasion (e.g. canvas noise).
Anonymous and identifiable events
Trueguard accepts both anonymous (attempt) and identifiable (success) events. Use anonymous events to record attempts before a user completes registration, and send identifiable events once the user is created so Trueguard can correlate activity across sessions and detect patterns like multiple accounts per device.
Why two event types?
Recording an anonymous registration attempt helps you spot suspicious behavior early (bulk registrations, automated signups, disposable emails) without creating accounts in your database. When a registration is completed, send a registration success event that includes the user's unique identifier so Trueguard can track that user over time and correlate signals (for example: multiple_accounts_per_device).

