Technical Guide to Residential Proxies: Architecture and Mechanics
1. What is a Residential Proxy?
At its core, a residential proxy is an intermediary server that uses an IP address provided by an Internet Service Provider (ISP), such as Verizon, AT&T, Comcast, or Vodafone, directly to a homeowner or subscriber.
Unlike datacenter proxies, which are hosted on cloud servers (AWS, Google Cloud) and have IP addresses associated with data centers (identifiable by their ASN), residential proxies route traffic through physical devices—desktop computers, laptops, mobile phones, or IoT devices—located in real physical locations.
Key Characteristics
- ASN (Autonomous System Number): The IP belongs to a consumer ISP, not a hosting company.
- Geo-Specificity: Because these are real homes, they allow for hyper-local targeting (Country > City > Zip Code).
- Legitimacy Signals: Requests originating from these IPs carry the same TCP/IP fingerprint and trust score as a normal human user browsing the web.
2. How the Architecture Works
Residential proxies do not operate like traditional server-based proxies. They rely on a Back-connect Architecture and a Peer-to-Peer (P2P) Network.
The Back-connect Gateway
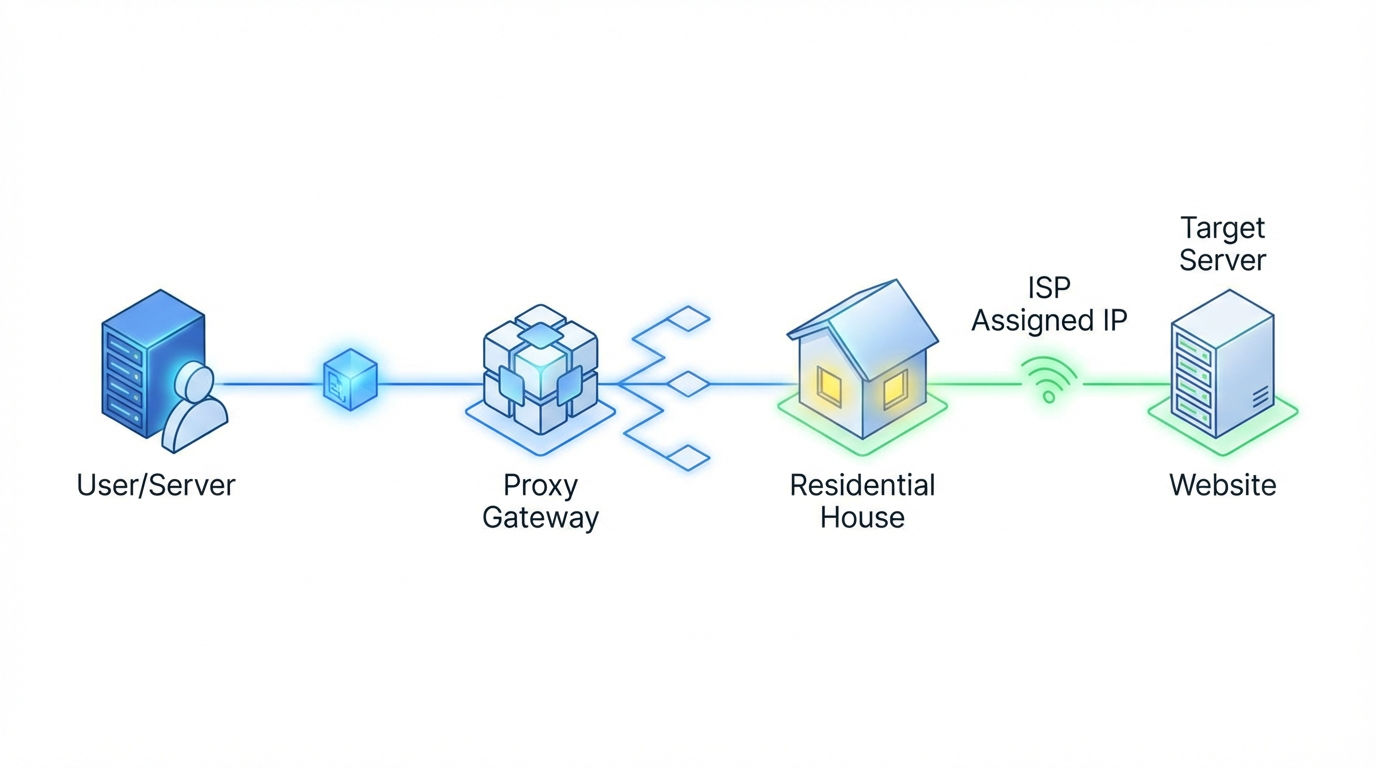
Users of residential proxies rarely connect directly to the specific residential IP. Instead, they connect to a Gateway Node provided by the proxy service.
- Entry: You send your request (e.g.,
curl google.com) to the provider’s gateway (e.g.,us.proxy-provider.com:8000). - Rotation Logic: The gateway checks your configuration (geo-targeting, session duration).
- Tunneling: The gateway tunnels your request to an available residential device (a "Peer") currently online in the desired location.
- Exit: The request leaves the residential device, reaches the target website, and the response is routed back through the chain.
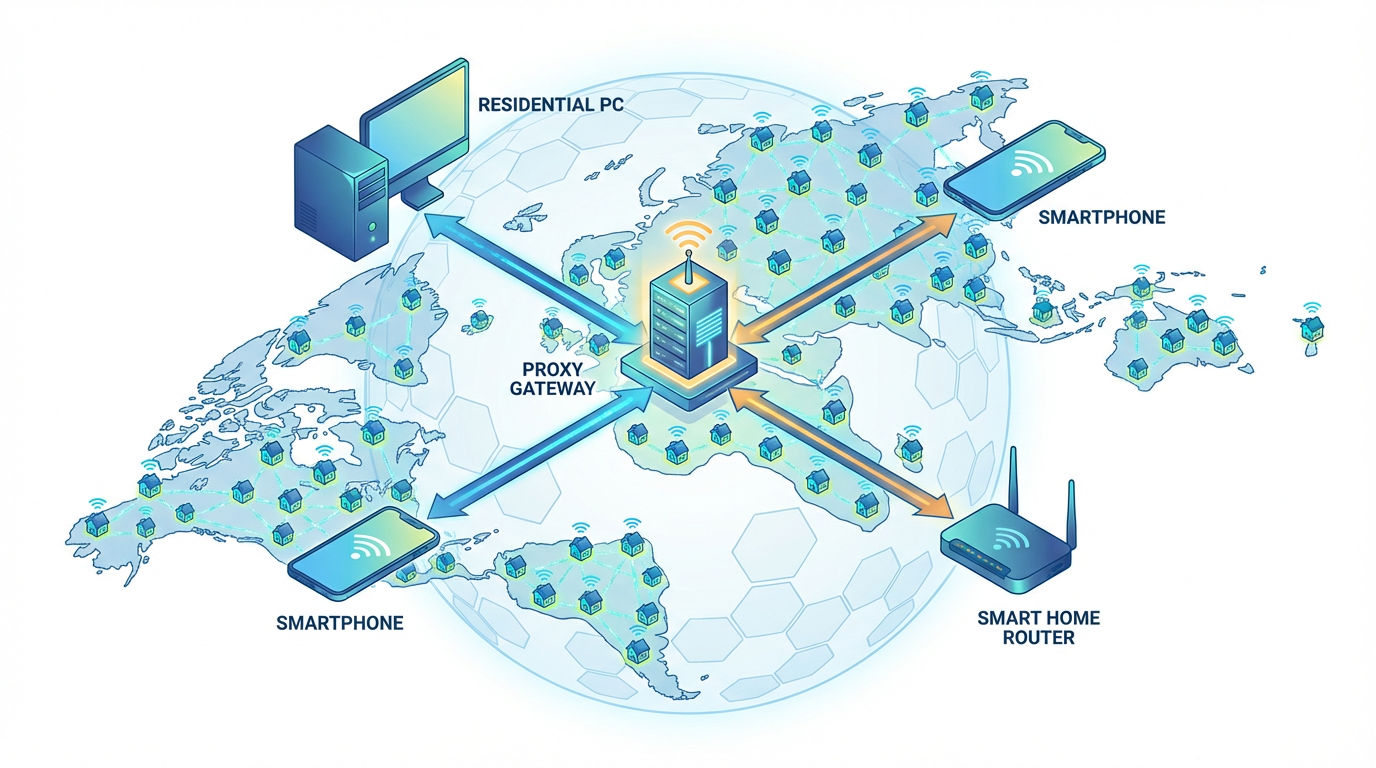
The Peer Network
The strength of a residential network lies in its pool of millions of devices. These devices are often sourced through ethical bandwidth-sharing SDKs. Users of specific apps may opt-in to share a portion of their idle bandwidth in exchange for premium app features or ad-free experiences. This creates a dynamic network where nodes (IPs) come online and go offline as real people turn their devices on and off.
3. Types of Residential Proxies
Residential proxies are categorized based on how the IP address is allocated and how long it remains active.
A. Rotating Residential Proxies
This is the most common type. The gateway assigns a new IP address for every new connection request or after a short, undefined period.
- Mechanism: If you send 100 requests to a website, the gateway routes them through 100 different households.
- Use Case: High-volume data scraping where maintaining a persistent session is not required, but avoiding rate-limits is critical.
B. Sticky Sessions (Time-based Rotation)
In this configuration, the proxy provider attempts to keep the user on the same residential IP for a set duration (e.g., 10 minutes or 30 minutes).
- Mechanism: The gateway binds the user's port to a specific peer device. If the peer device goes offline (e.g., the homeowner turns off their PC), the session drops or is forcibly moved to a new IP.
- Use Case: Actions requiring a login session, such as navigating through multiple pages of a retailer to verify checkout flows.
C. Static Residential (ISP Proxies)
These are a hybrid. They use residential ASNs (consumer ISPs), but the IPs are hosted in a data center environment rather than on a user's home device.
- Mechanism: The provider leases IP blocks directly from ISPs but hosts them on servers.
- Benefit: You get the speed and stability of a datacenter proxy with the trust score of a residential IP.
- Drawback: They lack the vast diversity of a P2P network.
4. Legitimate Use Cases & Industry Utility
Residential proxies are essential infrastructure for many modern data-driven industries. They solve the "Viewability" problem—seeing the web as a real local user sees it.
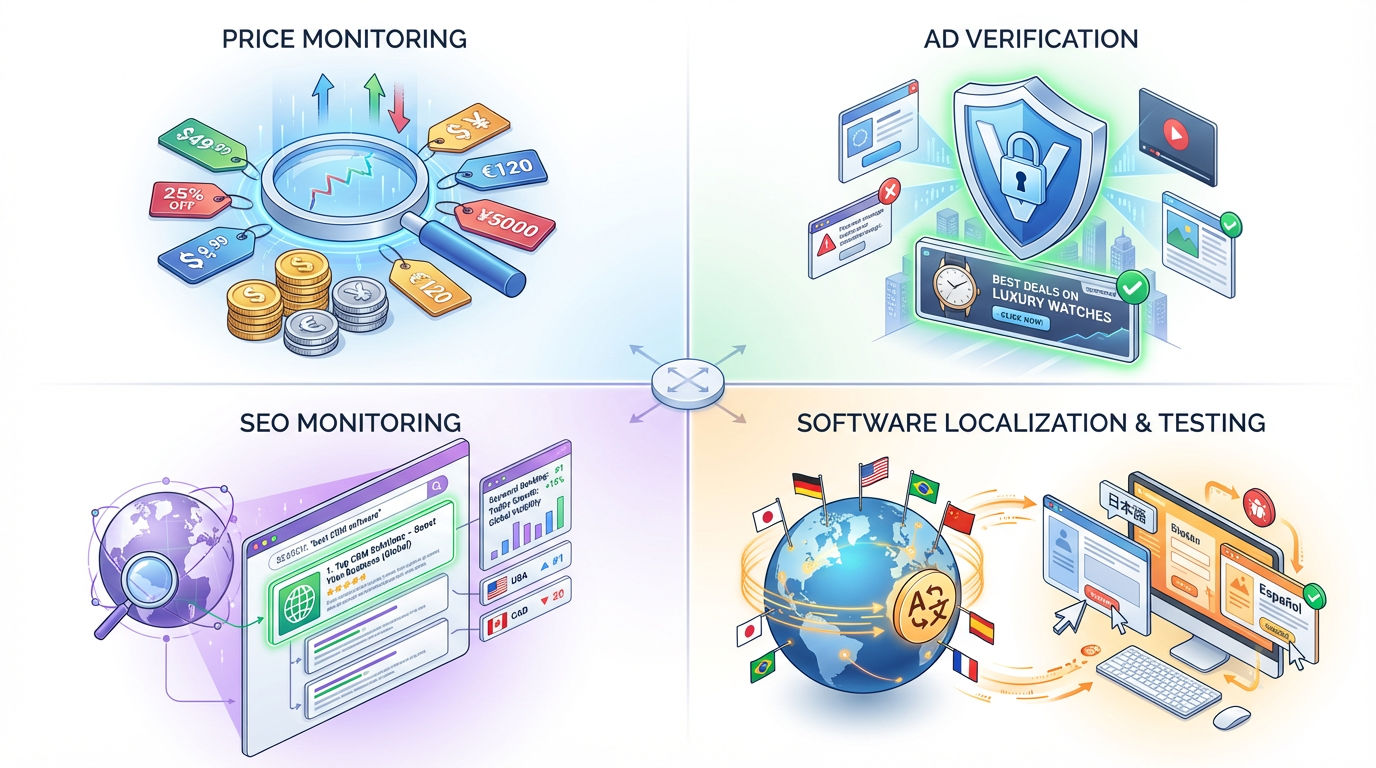
A. Market Research and Price Monitoring
E-commerce platforms display different prices based on user location, browsing history, and device type.
- The Application: Aggregators use residential proxies to scrape pricing data from competitors. By simulating real customers in New York, London, and Tokyo, businesses ensure they are getting accurate, unbiased pricing data rather than "bot-cloaked" data.
B. Ad Verification
Advertisers pay billions for ads to be shown to specific demographics. Bad actors often display these ads on invisible parts of a page or in the wrong countries.
- The Application: Ad tech companies use residential proxies to scan websites from specific residential locations (e.g., a residential IP in Berlin) to verify that their ads are appearing correctly and are compliant with local regulations.
C. SEO Monitoring (SERP Tracking)
Search engines (Google, Bing) tailor search results (SERPs) based heavily on the user's precise location.
- The Application: SEO agencies use residential proxies to check keyword rankings. A search for "best pizza" yields different results in Chicago vs. Miami. Residential proxies allow the agency to accurately track local rankings for their clients without being blocked for automated queries.
D. Software Localization & Testing
Developers must ensure their apps and websites function correctly for users in different regions.
- The Application: QA teams use residential proxies to verify that currency conversions, language translations, and geo-fenced content (like video streaming availability) trigger correctly for users in the target region.
5. The Malicious Application: Fraudulent Usages
Despite their utility in legitimate data collection, the defining feature of residential proxies—high-trust, ISP-assigned IPs—makes them the foundational tool for sophisticated automated attacks. Fraudsters leverage the IP’s perceived legitimacy to bypass IP-based rate limiting, geo-fencing, and basic bot detection systems.
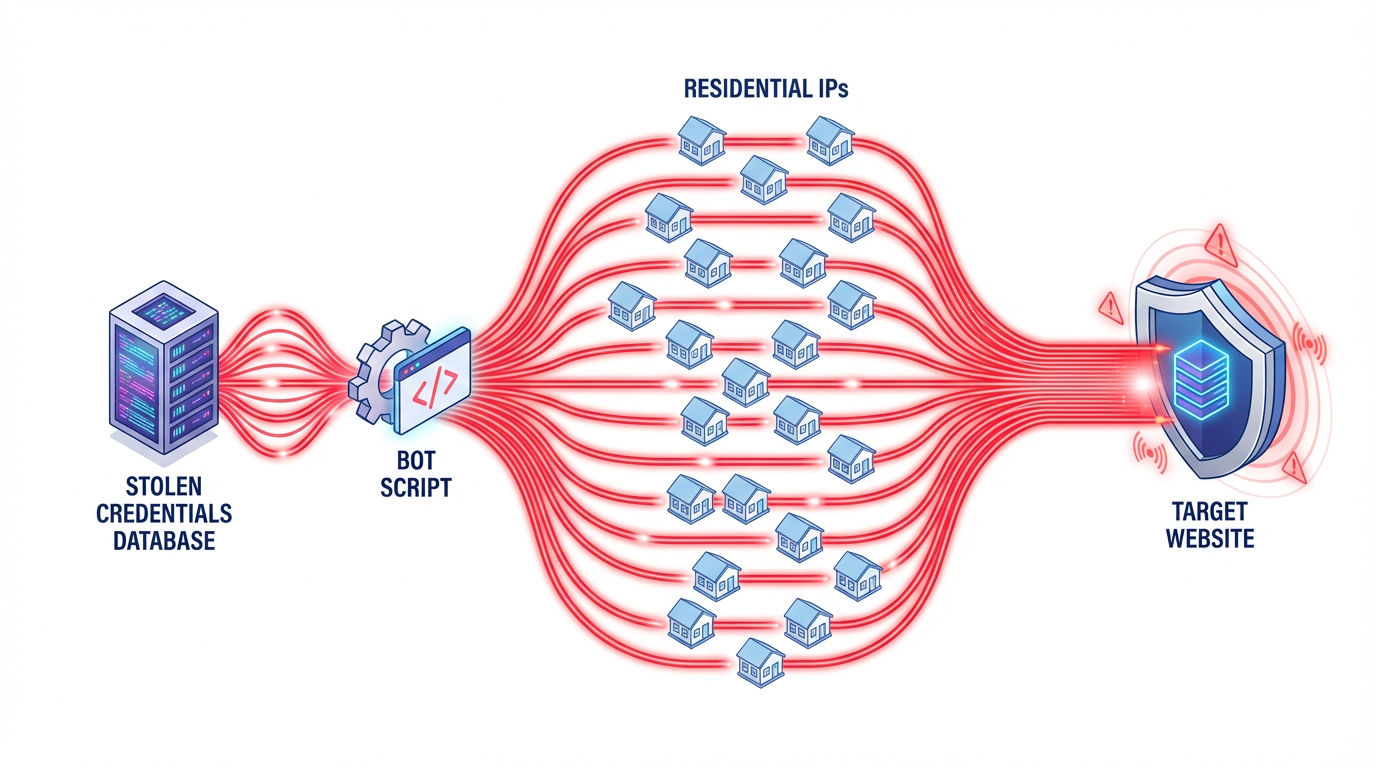
A. Credential Stuffing and Account Takeover (ATO)
This is one of the most common and damaging applications of residential proxy networks.
- The Mechanism: Attackers acquire massive lists of leaked username/password combinations ("combolists") from data breaches. They use automated bots to rapidly test these credentials against high-value targets (e-commerce, banking, streaming services).
- The Proxy Advantage: If an attacker attempts 10,000 logins from a single datacenter IP, the target server immediately flags and bans the source IP. By routing each login attempt through a different, rotating residential IP, the traffic appears to the security system as 10,000 individual users logging in from 10,000 different homes across the globe. This volume-based bypass is virtually impossible to detect without advanced behavioral analysis.
B. Ad Fraud and Traffic Hijacking
The goal is to illegally drain advertiser budgets by generating fake traffic that appears organic and premium.
- The Mechanism: Fraudulent publishers create automated scripts that simulate human browsing behavior: scrolling, mouse movements, and clicking on ads. They pipe this bot traffic through residential IPs located in high-value geographical markets (e.g., U.S. or U.K.).
- The Proxy Advantage: Advertisers pay a premium for impressions and clicks originating from these residential IP locations because they signify a real, desirable consumer. The residential proxy network allows criminals to generate millions of "premium" impressions and clicks that trick the ad network's verification and billing systems.
C. Scalping and Inventory Hoarding
When retailers release limited-edition, high-demand items (e.g., concert tickets, sneaker drops, electronics), they often implement strict controls, such as one item per IP address or per household.
- The Mechanism: Scalpers deploy automated buying bots ("scalper bots") connected to massive residential proxy pools. Before the item is released, the bot network secures thousands of unique residential IPs.
- The Proxy Advantage: The bot can simultaneously submit thousands of checkout requests, each using a distinct, legitimate-looking IP. The retailer’s system sees thousands of different "customers" and is overwhelmed, allowing the bots to acquire the entire inventory instantaneously before legitimate buyers can react.
6. Technical Comparison: Residential vs. Datacenter
| Feature | Datacenter Proxies | Residential Proxies |
|---|---|---|
| IP Source | Cloud Servers (AWS, Azure) | Real Consumer Devices (ISPs) |
| Anonymity | Low (Easily identified as a server) | High (Indistinguishable from users) |
| Speed | Extremely Fast | Variable (Depends on peer's WiFi) |
| Reliability | 99.9% Uptime | Variable (Peer may go offline) |
| Cost | Low | High (Due to sourcing complexity) |
| Block Rate | High | Low |
Summary
Residential proxies represent the most sophisticated tier of web traffic routing, founded on genuine, ISP-assigned IP addresses. Unlike easily identifiable datacenter IPs, residential IPs gain their high trust score from being routed through dynamic, decentralized Peer-to-Peer (P2P) networks, making them appear as organic user traffic.
This guide detailed the back-connect architecture, which manages the complex rotation and tunneling across millions of devices, and clarified the distinct types: fast-changing Rotating Proxies ideal for scale, and stable Static ISP Proxies essential for persistence.
This inherent trust imbues residential proxies with a powerful duality. They are an indispensable tool for legitimate operations, enabling accurate global market research, rigorous ad verification, and precise SEO localization. However, this same attribute makes them the central infrastructure for modern automated fraud, allowing large-scale attacks like credential stuffing and inventory scalping to bypass traditional IP-based security defenses.
For systems dedicated to defense, the takeaway is clear: residential proxy traffic cannot be countered by simple IP blacklisting. Effective protection requires advanced, real-time behavioral modeling and comprehensive device fingerprinting to differentiate a legitimate user from a malicious bot masking behind a trusted residential IP.
Frequently Asked Questions
The key difference lies in the IP address owner. Datacenter proxies use IP addresses registered to commercial hosting providers (cloud servers) and are easily flagged. Residential proxies use IP addresses assigned by real Internet Service Providers (ISPs) to homeowners, making the traffic appear organic and much harder to detect or block.


