Mapping the Disposable Email Ecosystem: Insights from 1.5 Million Emails
Disposable emails have become a key part of the modern internet. People use them to protect their privacy, while fraudsters use them to avoid being detected. To understand how these temporary inboxes influence online environments, we analyzed 1.5 million emails sent to disposable addresses from 46k+ websites across various industries.
Our analysis shows where disposable emails are most prevalent, including AI tools, SaaS platforms, dating sites, e-commerce, and more. It also reveals the types of messages they receive, ranging from free trial confirmations to password resets. The findings highlight not only how users briefly engage with platforms, but also how fraudsters misuse disposable addresses to bypass verification and take advantage of free services.
By uncovering these patterns, we hope to help platforms see what is often hidden: the behaviors and risks that come with throwaway accounts. This research emphasizes the need for proactive fraud detection, which is what Trueguard was designed to provide. It helps companies identify and block high-risk users in real time.
Key Takeaways
- Scale of the study: We analyzed 1.5 million emails sent to disposable addresses from 46,000+ websites across various industries.
- Top categories: AI tools, dating sites, and marketplaces showed the highest use of disposable emails. This is often linked to free-trial abuse and multiple accounts.
- Common message types: Most messages included signups, password resets, and free trial confirmations. This suggests short-term or possibly fraudulent engagement.
- Security risk: Disposable emails are not private or secure. Many inboxes are open to the public and can reveal OTPs, receipts, and refund confirmations.
- Real-world abuse: Fraudsters use disposable addresses to get around verification and take advantage of free services. They extract value before getting refunds, as shown by a €1,248 refund scam in our data.
- Defensive implication: To prevent abuse effectively, organizations need to go beyond simple email checks. They should combine network, device, and bot signals to identify and block high-risk users early.
What Are Disposable Emails?
Disposable emails are temporary inboxes that let users receive messages without revealing their real email address. They're designed for short-term use - often lasting just minutes or hours - and are popular for situations where people want to avoid spam, sign up for trials, or stay anonymous online.
There are two main types of disposable email setups:
- 1. Domain-based disposable emails: These come from dedicated temporary email domains such as temp-mail.org, 10minutemail.com, or guerrillamail.com. For example, a typical disposable email might look like
nijep42763@temp-mail.org. Anyone can generate and access these inboxes without authentication, making them easy to use - and easy to abuse. - 2. Temporary Gmail addresses: Some temporary email providers use real Gmail accounts to simulate disposable behavior. They rely on Gmail's dot and "+" aliasfeatures to generate endless variations of the same base address - for instance,
sh.i.e1.11.98.6@gmail.comorshie111986+asd123@gmail.com. These addresses all route back to a single inbox but appear unique to external systems, allowing users (or bots) to create multiple “different” accounts on the same platform.
While disposable emails can have legitimate uses - like protecting privacy or testing workflows - they also present challenges for platforms that rely on email verification for user trust and fraud prevention. Because they're easy to create and discard, disposable emails are often associated with fake signups, abuse of free tiers, and large-scale automation activity.
Methodology - How We Collected and Analyzed the Data
To better understand how disposable emails are used across the web, we scraped data from multiple public temporary email providers over a period of several months. These providers host openly accessible inboxes, allowing anyone to view incoming messages to randomly generated addresses. All data was gathered from public sources.
For each email observed, we extracted and stored key metadata, including:
- From and To email addresses - identifying the sender and the disposable address that received the message.
- Subject line - used to classify the email type (e.g., registration, password reset, or marketing).
- Email body - analyzed for language patterns and purpose indicators.
- Timestamp - the date and time the message was received.
Each message was stored in a structured database for large-scale analysis. In parallel, we also scraped metadata about the sender domains themselves. This included a short description of each domain (derived from its public website or metadata) and a high-level category such as AI, SaaS, e-commerce, dating, fintech, etc. Categorizing the senders allowed us to visualize which industries most frequently interact with disposable inboxes.
Who Sends Emails to Disposable Addresses?
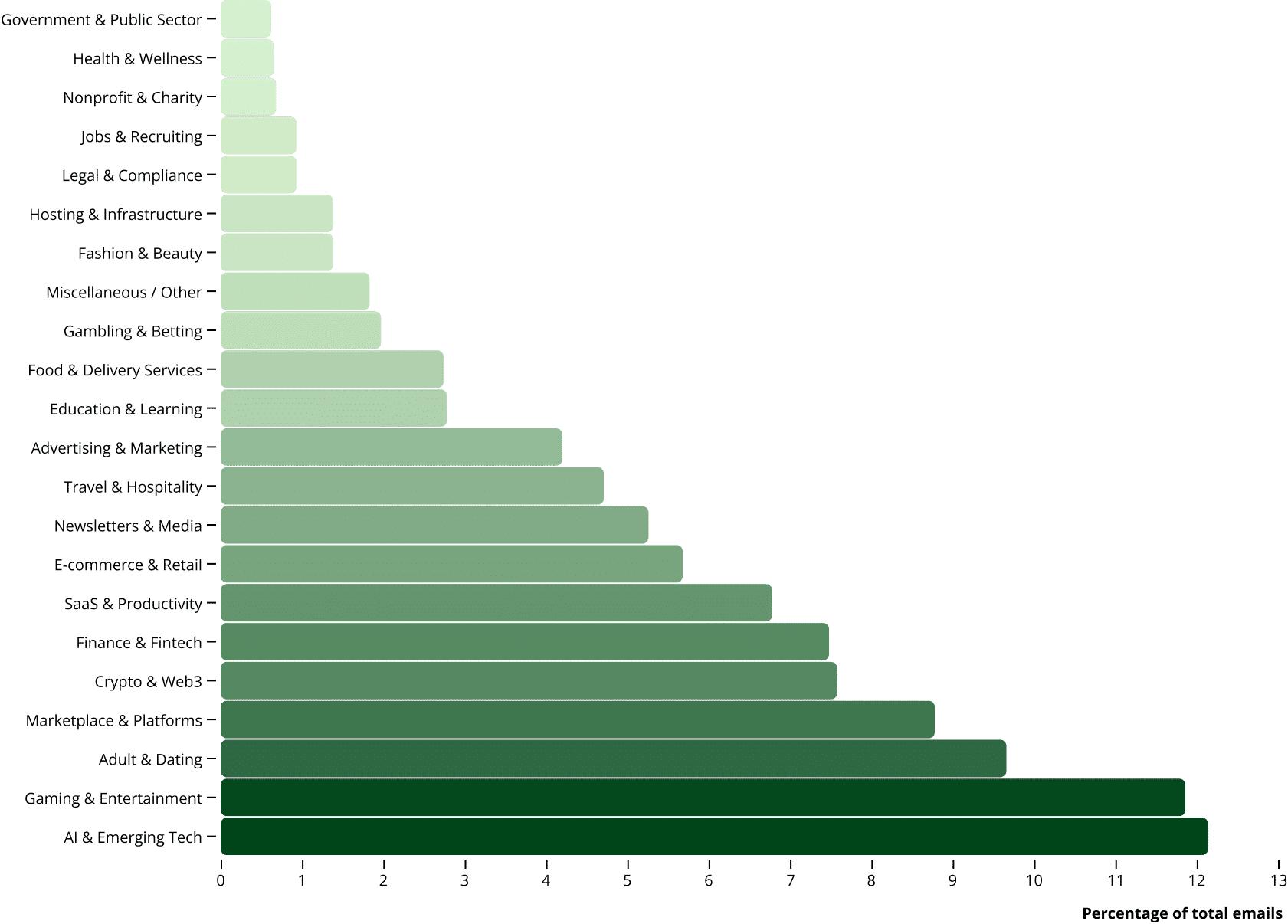
To understand which industries interact most frequently with disposable inboxes, we categorized every sender domain into one of several high-level segments - spanning SaaS, AI, e-commerce, finance, gaming, and more. This classification allowed us to identify which types of platforms are most exposed to disposable email traffic and how that activity varies by category.
The chart below illustrates the relative share of disposable email traffic across industries, based on more than 1.5 million messages analyzed.
The data shows that Marketplaces & Platforms, AI & Emerging Tech, Adult & Dating, and Gaming & Entertainment dominate disposable email activity - collectively accounting for nearly half of all messages received.
- AI & Emerging Tech (12.1%) - A fast-growing category reflecting the recent boom in AI-powered tools and APIs. High disposable email usage likely stems from users creating quick test accounts or exploiting free credit tiers.
- Gaming & Entertainment (11.9%) - Game and media platforms show significant disposable activity, often linked to free trial abuse, promo code farming, and repeated registrations to unlock bonuses.
- Adult & Dating (9.7%) - Disposable emails are heavily used to create anonymous accounts or bypass verification. These platforms often face persistent account churn driven by privacy-conscious users and spammers alike.
- Marketplaces & Platforms (8.8%) - Online marketplaces and service platforms generated the largest share of disposable email traffic. Many of these emails were registration confirmations or transactional updates, suggesting widespread testing or multi-account behavior among sellers and buyers.
- Finance & Fintech (7.5%) and Crypto & Web3 (7.5%) - While smaller in total sender count, both sectors show meaningful disposable usage. In these contexts, temporary emails often signal attempts to create multiple accounts or bypass KYC-linked signups.
- SaaS & Productivity (6.8%) - Disposable usage here typically correlates with free trial or freemium abuse, where users rotate emails to maintain indefinite access.
- E-commerce & Retail (5.7%) - Retail sites show moderate levels of disposable email activity, mainly for promo code redemption, newsletter signups, and one-time orders.
- Education & Learning (2.8%) - Many educational tools and platforms appear in the dataset, often associated with one-off trial usage or temporary access for testing learning management systems.
Other notable categories - such as Advertising & Marketing, Hosting & Infrastructure, and Newsletters & Media - appear frequently but with smaller relative volume. Even lower-frequency categories, like Health & Wellness, Government, and Legal & Compliance, demonstrate that disposable email usage extends well beyond consumer-facing apps into almost every sector of the web.
Percentage of total emails sent to disposable addresses
Percentage of total domains sending emails to disposable addresses
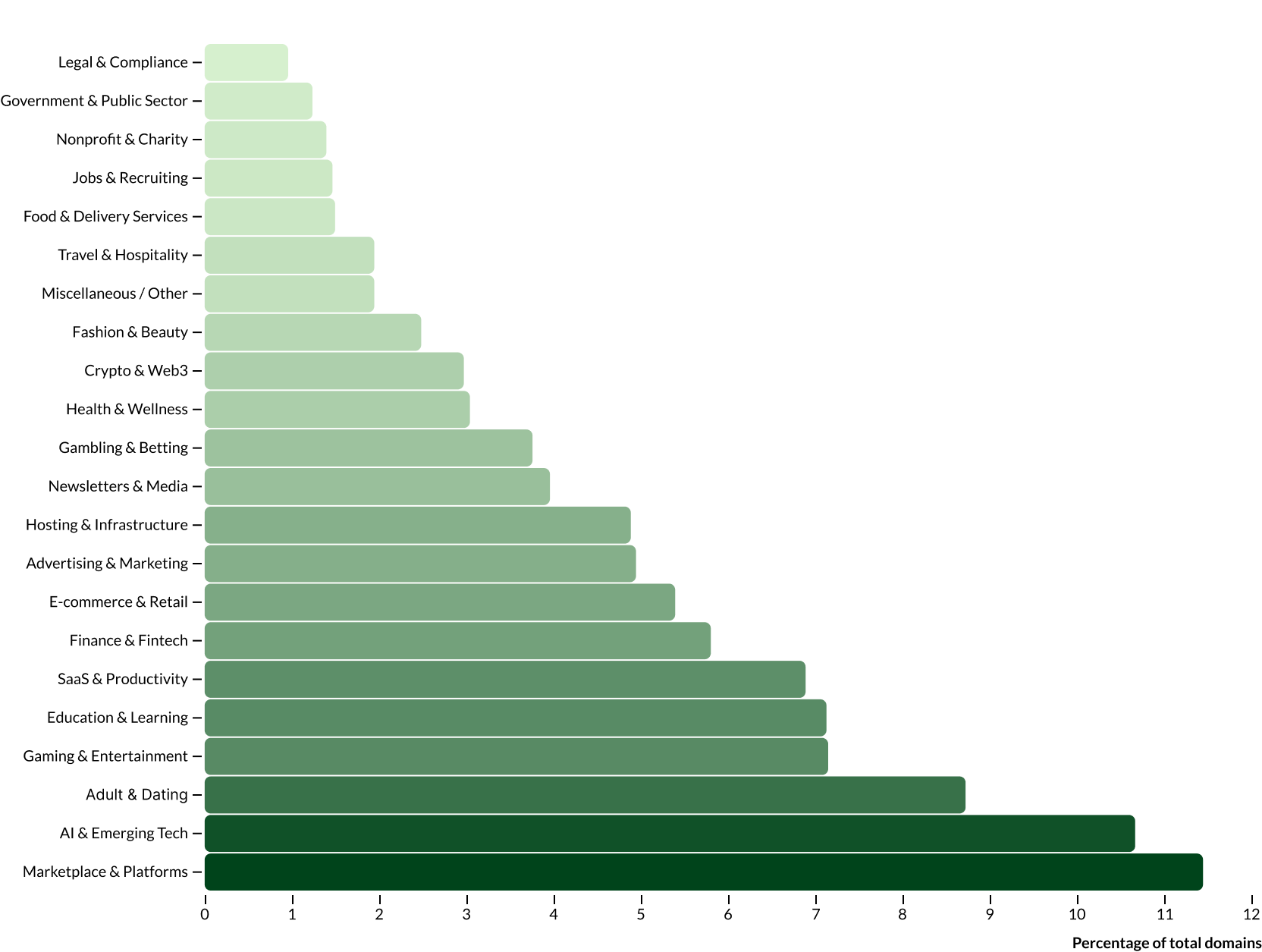
Overall, this data highlights how disposable email usage isn't limited to one type of platform. From productivity tools and learning portals to dating apps and gaming services, nearly every digital vertical sees some level of temporary or anonymous user activity - a clear signal of the need for adaptive fraud prevention.
What Kinds of Emails Are Being Sent?
Not all disposable emails are used in the same way. Some only exist to bypass account verification, while others receive transactional messages or sensitive notifications. To understand the types of messages sent to temporary inboxes, we analyzed emails and grouped them into common categories based on subject lines and content.
- Login confirmation (~160,000 emails) - One-time passwords (OTPs), two-factor authentication codes, and sign-in alerts sent when users log in or authenticate.
- Account registration / verification (~115,000 emails) - Emails confirming new signups, activating accounts, or verifying email addresses for new users.
- Free trial / onboarding (~70,000 emails) - Messages guiding users through trial activations, onboarding steps, or claiming free credits.
- Transactional (~25,000 emails) - Receipts, invoices, order confirmations, billing statements, and subscription notifications sent after purchases or service use.
- Data removal (~15,000 emails) - Requests or confirmations for deleting user data from a platform.
- Password reset (~10,000 emails) - Links and instructions to reset forgotten or compromised passwords.
- Account security alert (~5,000 emails) - Notifications about suspicious activity, unusual sign-ins, or security updates to protect accounts.
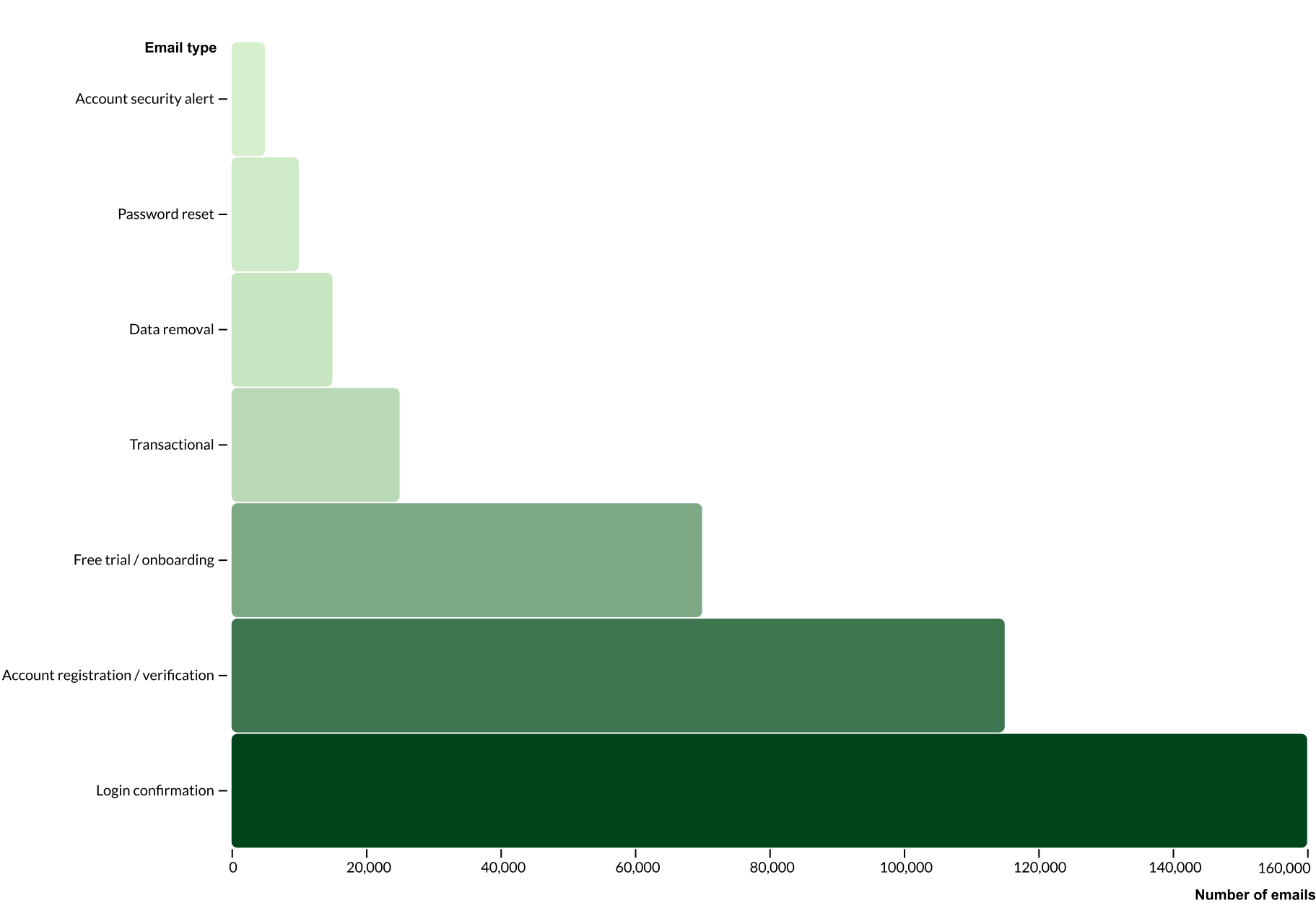
This distribution shows that disposable emails aren't just used to avoid marketing messages. They often receive important communications, transactional emails, and sensitive alerts. That makes them a valuable target for abuse, testing, and fraud across platforms.
Are Disposable Emails Really Secure?
Short answer: no. Disposable emails are not secure in the way most people assume. They provide convenience and a degree of anonymity for legitimate privacy-conscious uses, but they are fundamentally public or loosely controlled inboxes. That makes them a poor choice for any communication requiring confidentiality, long-term identity, or strong account assurance.
There are two structural reasons for this lack of security. First, domain-based temporary inboxes (for example, addresses issued by public services such as temp-mail.org) are openly accessible: anyone who knows or guesses the inbox identifier can view messages. Second, so-called temporary Gmail-style addresses created with dots or "+" aliases while routing to an existing Gmail account are still simple to generate and reuse, and they do not provide additional authentication beyond the base inbox.
Because disposable inboxes can be viewed or enumerated by third parties, the contents of those inboxes - including registration confirmations, reset links, receipts, or promotional messages - are exposed to risks that range from privacy breaches to downstream fraud. In our research, we intentionally worked only with data available from public inboxes and analyzed it in aggregate; we do not publish personally identifiable information and maintain ethical controls around data use.
What this exposure enables (high-level, non-actionable)
- Account enumeration and takeover risk: Public inboxes can reveal account-related emails (verification, password resets) that reduce the friction for attackers attempting account access - particularly when platforms rely solely on email-based assurance.
- Free-trial and promotion abuse: If an attacker can repeatedly create or access disposable addresses, they can cycle through trials, promo codes, or one-off benefits without long-term commitment.
- Transactional and financial leakage: Order confirmations, invoices, or receipts visible in a disposable inbox expose transactional metadata that can be misused for social engineering or fraud analytics.
- Data harvesting at scale: Because many disposable inboxes are public, automated processes can collect large volumes of messages and then analyze them for patterns to support abusive campaigns or targeted attacks.
Case Study - The €1,248 Refund Exploit
Among the messages collected in our dataset was a striking example of high-value abuse that illustrates how disposable addresses can mask malicious intent. We observed a disposable inbox receive a payment confirmation for €1,248.00 for a bulk-email verification service. The account proceeded to use the service intensively, and two days later the payment was refunded in full.
What happened (high-level timeline)
- Day 0: A disposable address receives a payment confirmation for €1,248.00.
- Day 0-2: The purchaser uses the service at scale (bulk verification activity consistent with normal customer usage).
- Day 2: A full refund is issued and the disposable inbox receives the refund confirmation.
- Immediate response: We notified the CEO of the affected company about the pattern; the CEO responded within 6 minutes requesting a calendar link to discuss next steps.
Impact
The company faced a direct financial loss of €1,248 due to a refund, even though the service had already been fully used during those two days. Essentially, the fraudster got the value of the product without paying for it. In addition to the monetary loss, the incident also increased the team's workload with refund handling, fraud investigation, and customer support follow-up. Cases like this show how one undetected abuse can lead to a double loss: lost revenue and lost time.
How Trueguard Helps Platforms Stay Ahead
As fraud tactics become more complex, relying on basic checks like email verification or IP blocking is not enough. Trueguard helps platforms stay ahead by combining intelligence across multiple layers. This includes data from email and network signals, as well as device and automation detection. With this approach, we can prevent abuse before it affects your business.
Key Capabilities
- Email Intelligence: Identify disposable, temporary, and low-quality email addresses in real time to block risky signups before they enter your system.
- Network Analysis: Detect VPNs, proxies, and suspicious IP clusters to uncover hidden sources of abuse and prevent repeat offenders from evading detection.
- Device Fingerprinting: Generate durable, privacy-safe device identifiers to spot multiple accounts from the same device and stop automated signup or usage patterns.
- Bot Detection: Identify bot-like behavior during registration or activity flows and block scripted signups. Do this without disrupting real users.
- Geolocation Intelligence: Monitor where users are connecting from and flag signups or transactions coming from high-risk or unusual regions.
- Risk Scoring: Combine email, device, and network signals into unified risk and bot scores that help prioritize investigations and automatically surface the highest threats.
- Rules Engine: Tailor fraud prevention to your product needs with custom rules that automatically block, flag, or review risky accounts before they cause harm.
Together, these layers of intelligence give platforms the visibility and control they need to combat sophisticated abuse. Trueguard continuously evaluates signals in real time. This helps teams stop disposable email signups, refund exploits, and automated attacks while keeping the user experience smooth.
Conclusion
Our research into more than 1.5 million emails sent to disposable inboxes shows just how deeply temporary email use is embedded across the modern web. Disposable addresses pop up in nearly every category, from AI tools and SaaS platforms to gaming and fintech. They are often part of legitimate testing or privacy efforts but are also commonly linked to abuse and fraud.
These findings present a key challenge for online platforms. Disposable emails mix genuine users with high-risk activity. When email identity is relied on as a trust signal, attackers can take advantage of this weakness. They can create throwaway accounts, cycle through free trials, or request fraudulent refunds while remaining largely undetected by traditional defenses.
The takeaway is straightforward: preventing this type of abuse needs a more thorough look at the signals surrounding each user, not just their email address. Device, network, and usage patterns all help us understand intent and build stronger defenses against evolving fraud.
Disposable emails are here to stay. However, with better data and smarter detection, platforms can turn what used to be a blind spot into a valuable source of insight. This can help them protect both their products and their users.
Frequently Asked Questions
Disposable emails are temporary addresses created for short-term use. They come from public services (e.g., temp-mail.org) or are simulated via Gmail aliases (using dots or + tags). People use them to avoid spam, test services, or preserve privacy, but they're also commonly used to mask abusive or low-intent activity.


