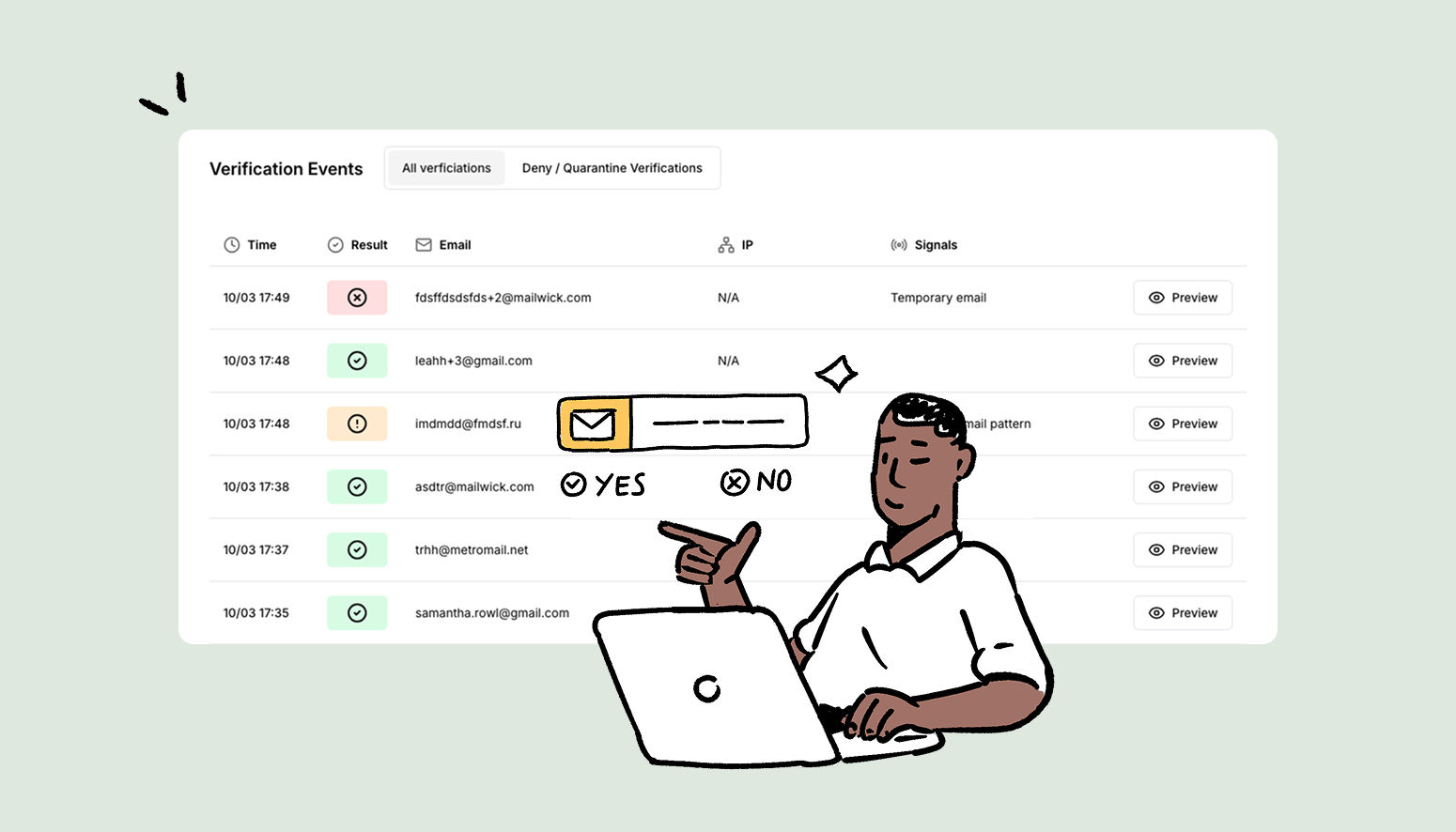
Preventing free-tier abuse with Trueguard
Key Takeaways
- Free-tier abuse has become a major threat for SaaS companies.
- Nothing is free! There are hidden costs inherent in providing any service for free. Infrastructure strain, operational expenses, and warped analytics from malicious users all add to these costs.
- Fake users and abusive accounts create real financial loss and eventually punishes real users and penalizes corporate profitability.
- To avoid misuse of free-tier services, it's essential to use various verification techniques. These can include email inteligence, analyzing IP addresses, and utilizing device and network fingerprinting methods.
- A balance between security and user experience is key. Best security measures stop bad actors while not inconveniencing legitimate users.
For Software as a Service (SaaS) companies, fake sign-ups, automated traffic and too many trial accounts not only hampers efficiency but also diminishes the quality of service available to genuine users.
The Sting of free-tier/freemium Abuse
Free-tier abuse is a constant battle to fight for SaaS businesses. It occurs when users abuse the free plan or free trial, usually in the most unmanageable fashion. As an example, automated account creation through the use of disposable emails.
Even less than 1% of free riders can siphon resources, illustrating the sustainability-killing effect of even minor abuse. B2C tools suffer, as bad actors exploit free-tier features that are intended for the good faith, quote unquote, customers.
At the heart of these abuses are different motivations for exploiting free tiers. Some users aim to test services without real intent to subscribe, while others abuse mechanisms like monthly credit resets or usage limits to gain repeated access without paying.
For example, SaaS that offers monthly free credits eventually become unsustainable as users avoid usage limits by creating or rotating through disposable accounts. These policies abuse infrastructure and undercut the value for actual paying customers.
In order to fix this, companies need to develop freemium abuse by design strategies. Captchas on signup forms are one method to prevent bot account creation. Blocking disposable/dedicated email domains is an ironclad best practice.
It's important to strike a balance between anti-abuse measures and user experience so that legitimate users aren't scared away.
When "Free" Isn't Really Free
Providing a free tier is usually a really good business strategy to garner new user adoption. However, it also invites challenges such as free trial abuse and multiple signups that can drain your staff's time and your company's money. Unfortunately, abusive fraud, including serious abusers using disposable email addresses and other methods, makes its way to seemingly-free services more often than you'd think, and the ramifications are deep.
The Hidden Costs of Fake Users
Fake accounts - which fraudsters can create in the thousands at little to no cost - can result in serious dollars lost. Instances have occurred where hundreds of thousands fake users were generated in just one day, resulting in significant financial losses for brands. Such accounts place a huge burden on infrastructure, hogging server space and doubling maintenance costs.
Misusing free-tier services leads to higher operational expenses, as companies have to deal with fraudulent signups and implement protective measures. Beyond financial concerns, the presence of fake users skews analytics, making it hard to gather meaningful insights. When businesses base their decisions on inaccurate data, it can result in misguided strategies, further harming their profits and overall success.
Technical Overload from Abuse
In high volumes, these non-authentic users can flood servers, degrading performance and reliability. As companies are pushed to absorb impacts of abuse, it requires expending resources such as security upgrades and enforcement of anti-abuse policies.
When a system is brought down, system uptime quickly becomes a problem impacting all users, including the law abiding ones.
From Frustration to Trueguard
Free-tier abuse has long been a frustrating reality for SaaS platforms, eroding both goodwill and development bandwidth. My personal story of getting behind Trueguard started with that same frustration. Running multiple SaaS projects, I encountered repeated cases of fake signups, bots exploiting free tiers, and malicious users draining resources without contributing value.
Building an Internal Solution
We tackled fraudulent registrations by identifying common tactics used by bad actors, like disposable email addresses, multiple accounts from one IP address, VPNs and more.
We created an internal codebase with strict rules to automatically flag suspicious behaviors during registration. We compiled a list of disposable email providers, validating emails against this list during sign-up. Users trying to register with these emails receive an error message encouraging them to use a different address.
To prevent multiple accounts from the same IP, we set a limit on registrations per IP address within a specific time frame, which helped us eliminate huge amount of abusive accounts. We also used IP insight services to block registrations from suspicious IPs linked to data centers or previous fraud.
Sharing the Solution with Others
Understanding that this was not a unique problem, I realized we had the chance to provide free-tier abuse detection service other SaaS providers. We made the decision to transform our internal solution into a standalone product, named Trueguard, allowing all SaaS companies to implement it effortlessly.
One early adopter, a mid-sized SaaS provider, eliminated >90% of free-tier abuse with the help of Trueguard, reducing costs and reclaiming time to focus on product development.
Trueguard: Protecting SaaS Companies
Trueguard's core strength comes from a combination of preemptive abusive blocking combined with the actionable insights it maintains on user experience. Its real-time detection feature, alongside its scalability, makes it perfect for businesses both large and small.
By protecting authentic users, Trueguard enables SaaS developers to shift their attention away from combating abuse and move toward growing their business and innovating.
From Personal Pain to Universal Protection
In this way, the process of Building Trueguard was very personal. Universal experiences fuelled by individual hurt. As so many of you, especially those that have worked on SaaS projects, can attest, I experienced firsthand how free-tier abuse drives developers from platforms.
Fake signups and harmful bots are not only bad for engagement. They squander resources, distort analytics, and damage real users. Beyond just a technical challenge, this had been a consistent personal pain point that required a forward-thinking property owners' solution. Trueguard was born out of this frustration, designed to directly solve these pains by providing true real-time protection that's automated and effortless.
The issue stretches past just these individual platforms. It's a problem that exists broadly across the industry. Many SaaS providers struggle with the same cycle: launching a free tier to attract users, only to have it exploited by bad actors.
Preventing Free-Tier Abuse: A Founder's Guide
With a free tier in your SaaS product, you really have a great low-friction way of getting users on board with your service.
Be careful of abuse, because it can rapidly incur high costs. Plausible abusive users can batch create tens of thousands of accounts on the free tier per day, saturating your resources and poisoning your platform.
Immediately below, I share some practical steps you can take to prevent free-tier abuse.
Verify Emails
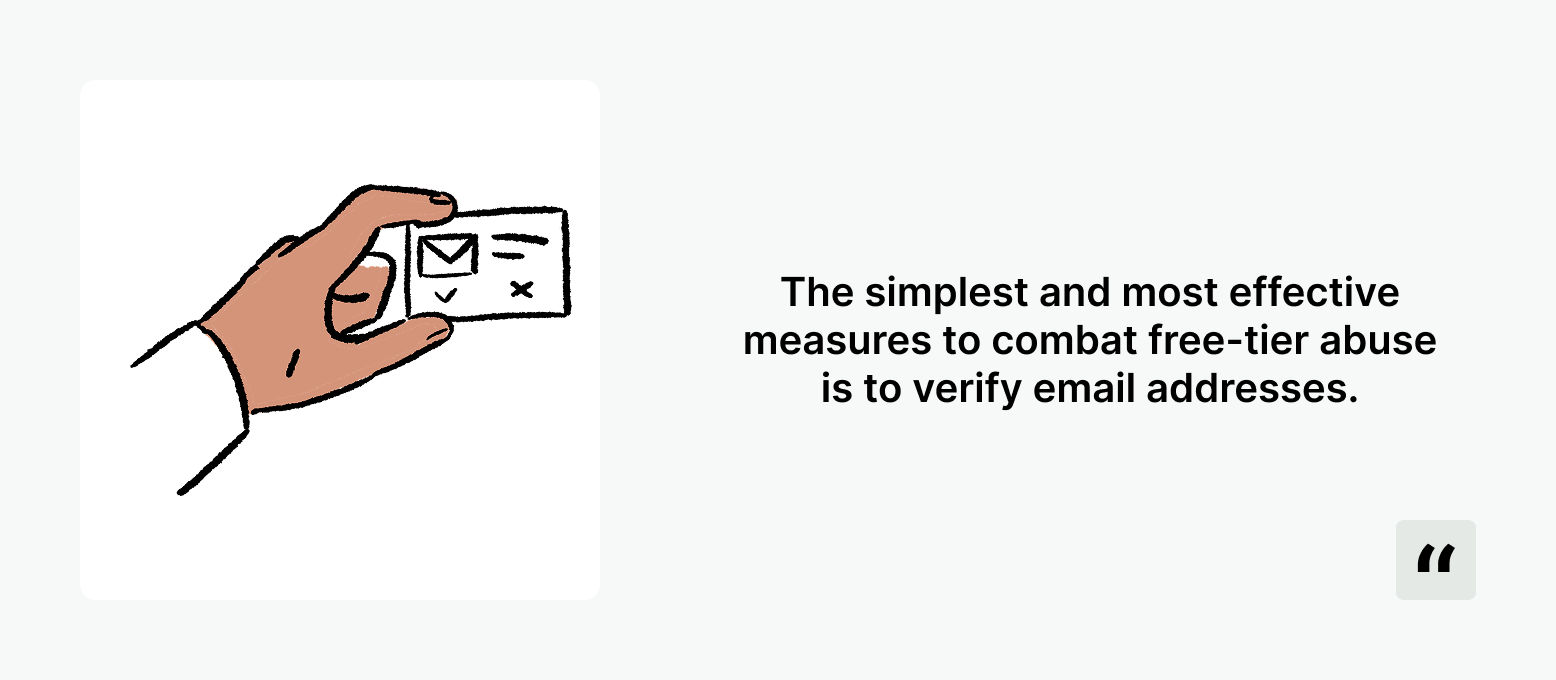
One of the simplest and most effective measures to combat free-tier abuse is to verify email addresses. Numerous open-source lists of temporary domains can be found on GitHub such as FakeFilter. Trueguard combines these open-source resources with our own database, continuously monitoring new domains around the clock.
However, it's important to remember that just verifying temporary domains isn't sufficient. There are also many services that provide temporary Gmail and Hotmail addresses. At Trueguard, we have identified ~10.000 such emails.
Additionally, tools like Apple's Hide My Email can create random email addresses for users, adding another layer of complexity.
Trueguard's Email Intelligence additionally assigns a high risk score to emails with random patterns, such as sdkfgjsdfgbnsd@gmail.com, because there is little likelihood that these belong to legitimate users.
Monitoring IP Addresses
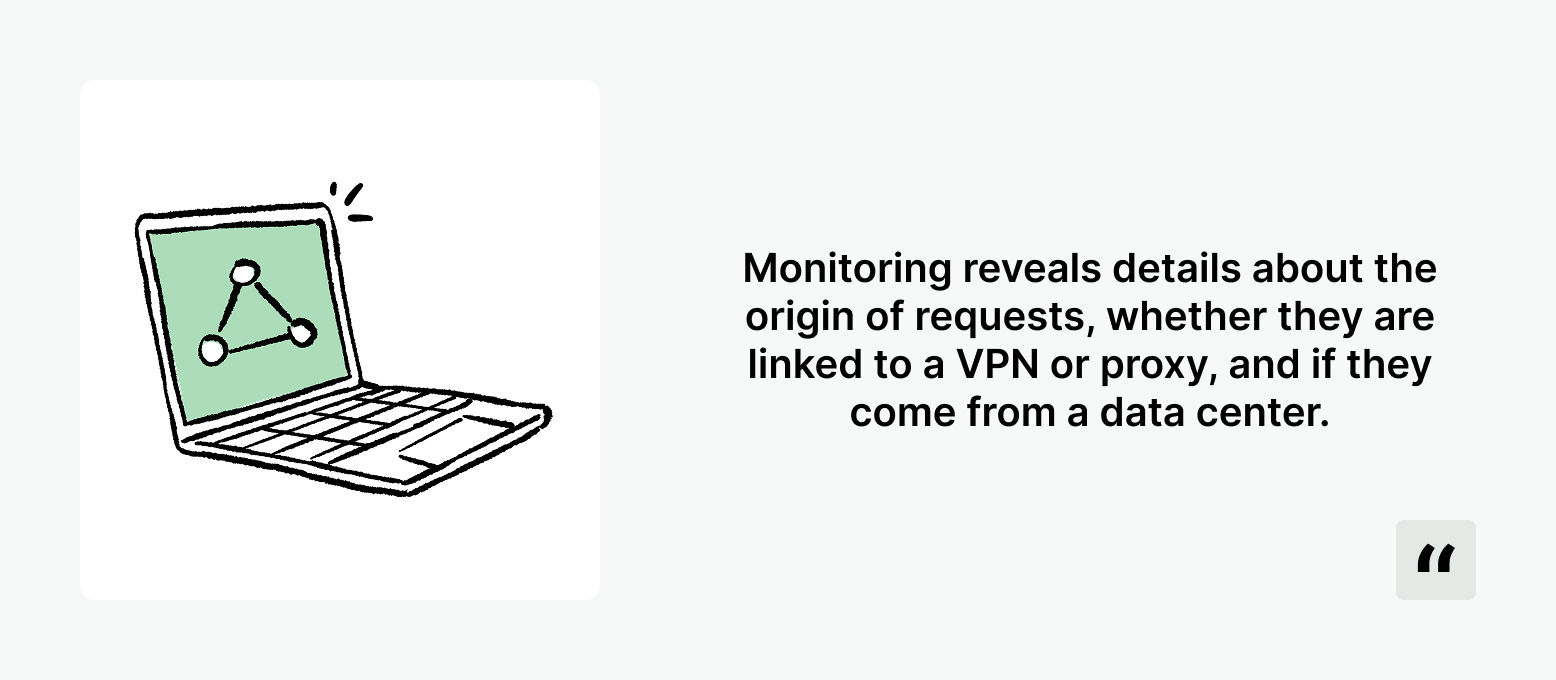
IP tracking is key to recognize patterns such as multiple signups originating from one address.
However, IPs offer more than just that. They reveal details about the origin of requests, whether they are linked to a VPN or proxy, and if they come from a data center.
By considering this information, businesses can effectively reduce instances of abuse.
Device and network fingerprinting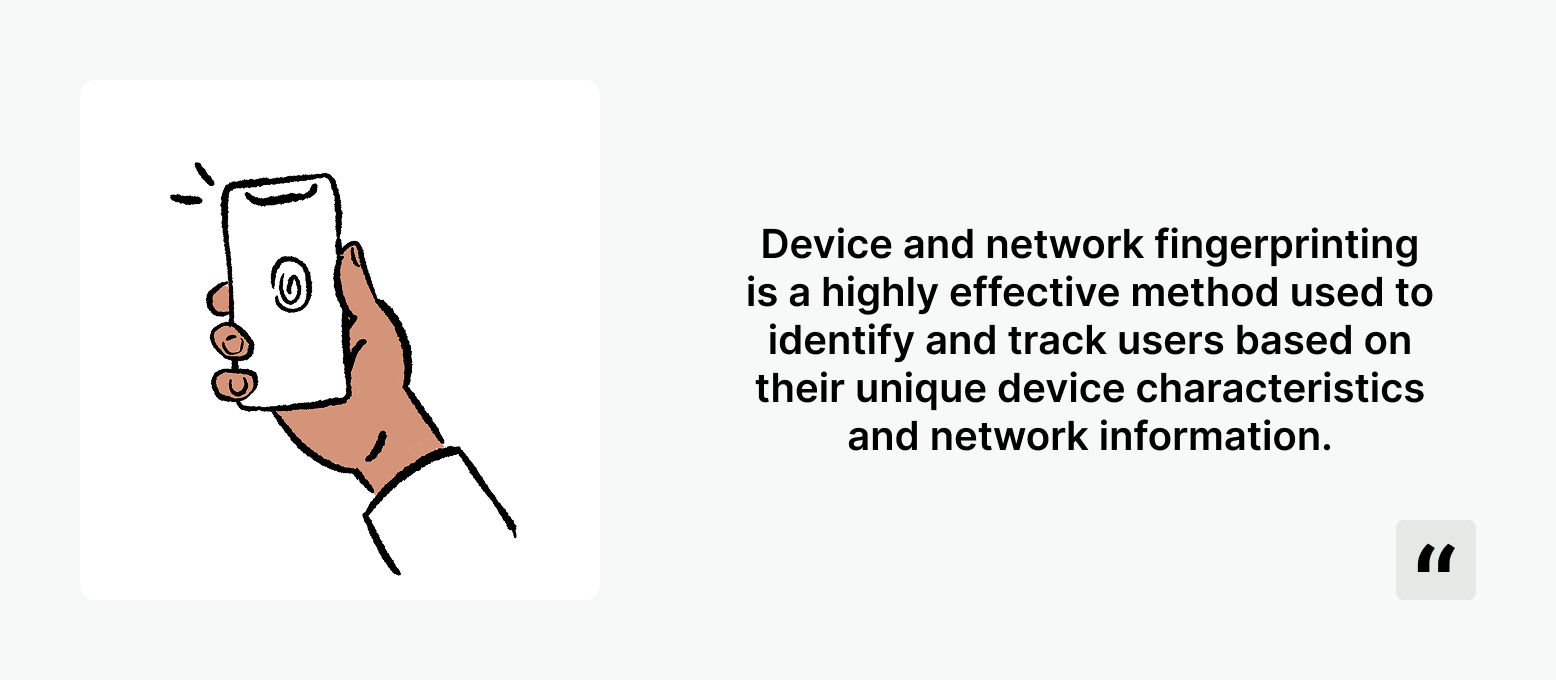
Device and network fingerprinting is very effective way of combating abuse as they are harder to fake for regular day to day users.
Device and network fingerprinting is a highly effective method used to identify and track users based on their unique device characteristics and network information.
This technology makes it challenging for those trying to abuse free-tier services, as it becomes difficult to impersonate regular users. By analyzing various factors like browser settings, operating system details, network characteristics, service providers, and more can pinpoint suspicious activity and prevent misuse.
Limit Free Tier Functionality
Limiting features available in the free tier makes it less tempting to would-be abusers.
Establish definitive boundaries, such as maximum allowed API calls or storage space, to manage how much users can benefit from unlimited resources.
Behavior-based tiered access prevention lets real users advance while stopping abusers in their tracks.
Implement CAPTCHAs Strategically
CAPTCHAs such as Google reCAPTCHA and Cludflare Turnstile stop bots in their tracks.
Adaptive CAPTCHAs change depending on the level of risk, allowing a smooth user experience without annoying legitimate users.
Alternatives such as invisible CAPTCHAs that only challenge suspicious traffic add an extra layer of security without adding user friction.
Require Payment Information

Asking for payment information when signing up for a free trial turns away these abusers who flinch at even a nominal fee.
Fraudulent credit cards are difficult to maintain, so this is a relatively inexpensive deterrent.
Challenges in Sustaining Free Tiers
While free tiers are indeed a powerful tool for attracting users, there are some notable challenges in sustaining them. Businesses may quickly become overwhelmed with challenges such as resource drain, exploitation by unsponsored users, and the inability to successfully transition free users into paying customers.
Unless free tiers are carefully designed, these hurdles can threaten the sustainability of these offerings.
Cost-Efficient System Design
Designing a cost-effective system to support continuity of free trial offerings is crucial. Automation will be critical for lowering operational costs and preventing free trial abuse. It is particularly adept at automating manual tasks such as tracking traffic trends, identifying anomalies, and optimally allocating resources.
For example, SaaS platforms can leverage automated fraud prevention systems to prevent abusive signups at the outset, limiting manual review efforts. Continuously monitoring the performance of the system is also essential. Regular evaluation of system performance helps pinpoint inefficiencies in troublesome projects.
For instance, platforms like Heroku and Koyeb faced abuse from mining gangs exploiting free compute resources, highlighting the need for ongoing optimization. A smart use of targeted resources means that true users get the advantages they're looking for without jamming up the system.
Scaling Resources Efficiently
Scaling resources for free-tier services will need thoughtful solutions that respond to demand shifts. Cloud solutions offer businesses the flexibility to rapidly respond by scaling up or down as circumstances require.
Load balancing takes performance even further, spreading out traffic across servers to eliminate potential bottlenecks. Proactive resource management - from regular usage reporting to implementation caps - can avoid misuse of the resources without putting a major financial burden on providers.
Heroku's recent decision to sunset its free tier is a sobering example of the difficulty in sustaining growth while managing resource constraints.
Maintaining Free Tiers Without Credit Cards
Offering free tiers without credit cards broadens accessibility but increases abuse risks. Clear policies, like establishing usage limits or only allowing access for verified accounts, can help prevent that.
Companies such as Dropbox stopped offering free trials to prevent abuse, illustrating how the abuse can lead to an inability to sustain something. If left unchecked, overly generous plans can do severe damage by not converting free users into paid customers.
Conclusion
Free-tier abuse isn't just an operational headache - it's a swift kick to trust, growth, and resources. Addressing it isn't just about banning users, it's about curating an environment that's equitable and long-term for all users. Striking the right balance between accessibility and robust safeguards requires time and careful automated technology.
Trueguard was birthed from that first hand frustration. From there, it became an approach that safeguards users while introducing no extra steps in their journey. From peace of mind to reduced complexity, it illustrates that security doesn't have to equal compromise - it can equal confidence.
If you're in charge of a platform with a free tier, don't wait until abuse gets out of hand. Begin planning today to ensure that you don't disrupt what you've innovated, but don't clunk up the experience for your end users. Making the right decisions today will go a long way toward ensuring their continued success for many years to come.
Frequently Asked Questions
Free-tier abuse, particularly through the use of disposable email addresses, is one of the ways free services get exploited, pushing them beyond their original scope and creating significant financial and operational burdens on companies offering free compute resources.


